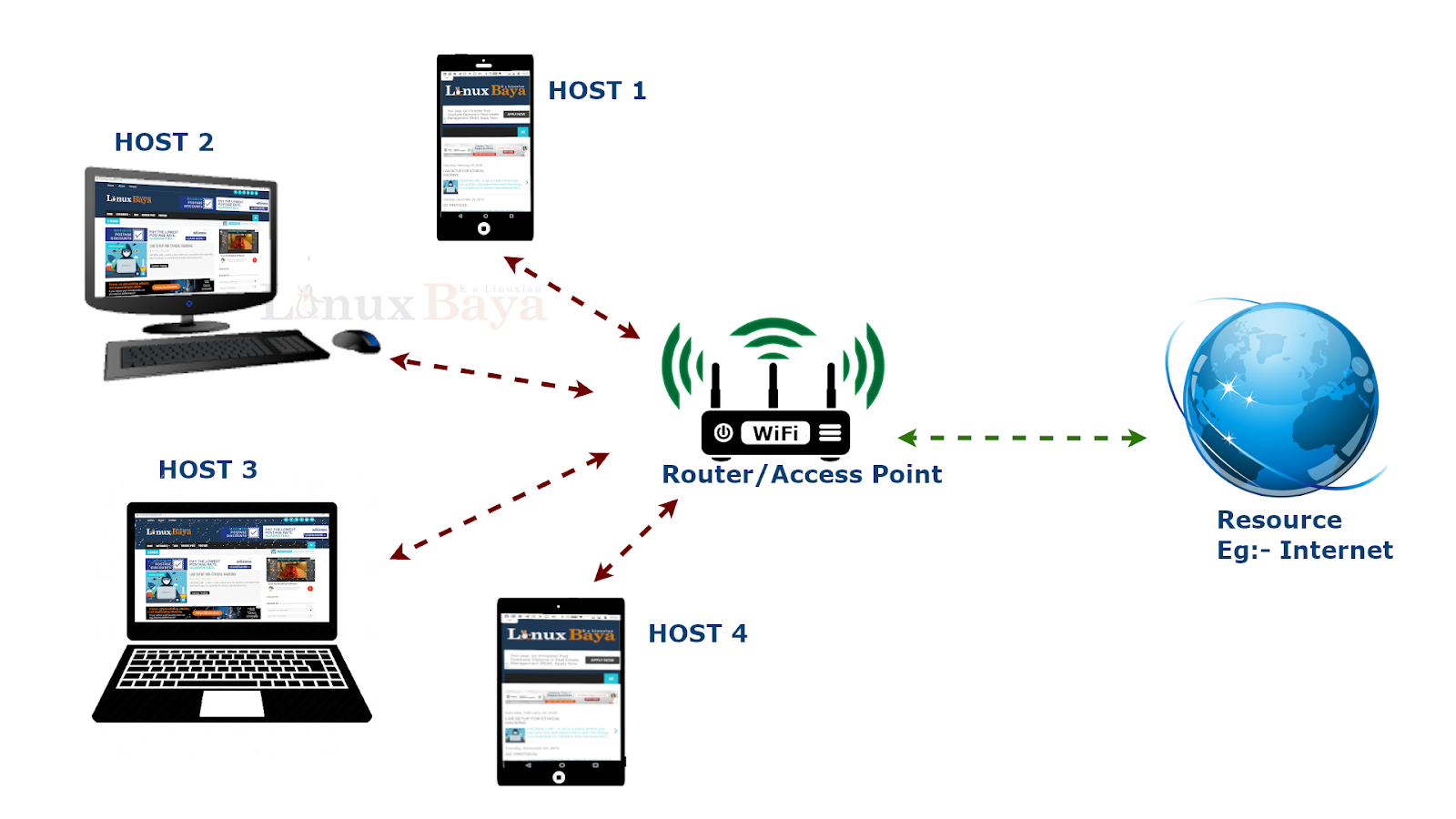
Now, before we start talking about network hacking, you need to have a basic understanding of how networks work. We all know that a network usually contains a number of clients connected to each other, and clients usually connect to a network in order to share data or share a resource. A really good example of a resource that we all have connected to networks in order to access is the internet.
So, we connect to Wi-Fi networks and even wired networks all the time just to access the internet. All networks work on the same principle. They have a device that is considered as a server. Now, in many cases, for example, in your home network, this server is your router. This is also referred to as an access point. Now, this router or server or access point is the only device that has access to the resource. So, none of these clients have direct access to the resource, even after connecting to the network. The only way they can access the resource is through the access point.
So, let's say, for example, you're host 3 and you connected to your home network over Wi-Fi or over ethernet, over a cable and then you opened your browser and you typed facebook.com. What happens is your computer will send the request to the access point asking for facebook.com. The access point has access to the resource, which is the internet in this example, so it's gonna go and look for facebook.com. It will receive facebook.com, and it'll forward that response to your computer, and as a result, you will see the website loading on your browser. So if you actually go to your router at home and look at it, you'll see at the back it's connected through a cable to the wall and this is how it's getting its internet access. Therefore, it is the only device in your network that has direct access to the resource and none of your computers, none of the computers connected to the network can access the resource or can access the internet without the router, without the access point.
So the only way for all of the connected clients to access the resource is to go through the router. Now, the data is transferred between clients and the access point as packets. So you can think of all of these arrows as a series of packets being transmitted between the client and the router as requests and responses. Now, in Wi-Fi networks, these packets are transmitted in the air. Therefore, if you have a wireless card and you're within range, you'll be able to capture all of these requests and responses. So, basically, you'll be able to see anything that any computer connected to the same network as you, thus on the internet, because they will have to send all of these data to the access point, and because they're sending this data in the air because you're in a WiFi network, you'll basically be able to capture these requests and responses. And you'll be able to see the URLs they visit, the usernames, the passwords they enter, the chat messages. Anything they do on the internet will be sent as packets and therefore you'll be able to capture it and analyze it.
To capture packet data, we need an external WiFi card connected to our attack machine. Because in internal network card does not support some features to capture the packet. So we need the following changes in our machine.
1. Change the MAC address of the wireless card.
MAC address stands for Media Access Control, it's a permanent, physical, and unique address assigned to network interfaces by the device manufacturer. So whether you have a wireless card, or a wired, or Ethernet card, each one of these network cards come with a specific address that is unique to this card. So there are no two devices in the world that would have the same MAC address. And this address will always be the same to this specific device, even if you unplug it from your computer, connect it to another computer, then this network device will always have the same address.
So being able to change your MAC address to another device's MAC address will allow you to impersonate this device and allow you to do things that you might not be able to do. So you'd be able to bypass filters or connect to networks that only specific devices with specific MAC addresses can connect to, and you will also be able to hide your identity.
How to do:-
1. Run the following command to see the list of network cards connected to your device.
ifconfig
2. Disable the wireless card to change it's MAC address. (wlan0 is the name of the wireless interface)
ifconfig wlan0 down
3. Change it's MAC with any number.
ifconfig wlan0 hw ether 00:11:22:33:44:55
4. Enable the interface.
ifconfig wlan0 up
5. Check the MAC address of that interface.
ifconfig
Remember the MAC address will revert back to its original address once you restart your machine because we only change the MAC address in memory not physically.
2. Change the mode of the wireless card.
As we discussed the wireless data transfer happens in the form of a packet. So each packet has a source MAC and a destination MAC and it flows from the source to the destination. If you're within range, then you'll be able to capture all of this communication because these packets are literally sent in the air. So we can just capture them even if they do not have our MAC address as the destination MAC.
To do this, we need to change the mode of operation of our wireless interface so that it operates in monitor mode.
How to do:-
1. Run below command to check the mode of the wireless adapter.
iwconfig
2. Disable the wireless card. (wlan0 is the name of the wireless adapter)
ifconfig wlan0 down
3. Run below command to kill any process that could interfere with using your interface in monitor mode.
airman-ng check kill
Now you'll notice when you're on this command, it'll actually kill the network manager. we will only need to be in monitor mode when we are running pre-connection attacks so attacks that do not require us to connect to any network. So we actually do not need an internet connection to run any of the attacks that require monitor mode.
4. Enable monitor mode.
iwconfig wlan0 mode monitor
5. Enable the wireless card.
iwconfig wlan0 up
6. Check interface mode.
iwconfig
Now, this is enough to get you going through some network attacks so that you can sniff data, analyze it, and start launching some cool pre-connection attacks. We'll discuss more networks attack.
Related posts:-